Hello!, this time i bring a new tool for editing and sending HTTP request, it's a simple tool that you can use to debug or compare raw request to the HTTP servers. It's useful to replace the usual telnet session where do you need to type everything every time you want to send a request. With this tool you can change a simple letter in the request and re-send it, just pushing one button.
It supports SSL and request/response history. It's based on python and pygtk.
This is the first version, if you liked or think that would be cool to add something else please write me :)
Get it from Here
Enjoy
Edge-security blog about Penetration testing, OSINT, security tools, and other interesting stuff.
Wednesday, June 14, 2006
Monday, June 12, 2006
Proxim wifi cards on Ubuntu Dapper
I received some Proxim Gold Orinoco B/G Pccard to test for wireless assessments, at first i try the card in my Ubuntu Dapper but it didn't worked. I read some how-to's but they recommended to use ndiswrapper, the problem of ndiswrapper is that don't support monitor mode :( .
Then i found Madwifi a Linux kernel device driver for Wireless LAN chipsets from Atheros, the Proxim card is based on atheros, cool. I downloaded and compiled the new version of the driver, the "ng" branch; all was ok, but when i tried to pass to Monitor mode it didn't worked. I tried some tips on some forums but no way..
I decided to install the old version of madwifi drivers, compiled them, try them, and all went OK!
So if you have a Proxim Gold card, i recommend to use the madwifi old version.
Then i found Madwifi a Linux kernel device driver for Wireless LAN chipsets from Atheros, the Proxim card is based on atheros, cool. I downloaded and compiled the new version of the driver, the "ng" branch; all was ok, but when i tried to pass to Monitor mode it didn't worked. I tried some tips on some forums but no way..
I decided to install the old version of madwifi drivers, compiled them, try them, and all went OK!
So if you have a Proxim Gold card, i recommend to use the madwifi old version.
Saturday, May 20, 2006
2D and 3D traceroute with Scapy
I was trying the scapy graphic traceroute features, and i liked both of them the 2D and the new 3D traceroute output.
Let's do a basic traceroute:
>>> mytrace,err = traceroute (["www.google.com"])
And the classic output is this:
>>> mytrace.show()
216.239.51.99:tcp80
1 192.168.1.1 11
2 87.219.30.1 11
3 10.255.136.254 11
4 10.255.228.1 11
5 10.255.228.2 11
6 208.175.154.177 11
7 195.2.10.122 11
8 195.2.10.129 11
9 195.66.226.125 11
10 72.14.238.253 11
11 66.249.95.146 11
12 216.239.49.34 11
13 66.249.94.235 11
14 72.14.238.232 11
15 72.14.238.97 11
16 66.249.95.149 11
17 72.14.239.17 11
21 216.239.51.99 SA
23 216.239.51.99 SA
24 216.239.51.99 SA
26 216.239.51.99 SA
29 216.239.51.99 SA
Now if we want to create a 2D image of the results we just do this:
>>> mytrace.graph(target=">mytrace.svg")

Better for understanding ;)
And for last the 3D output:
>>> mytrace.trace3D()
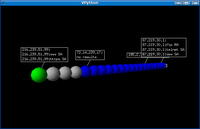
Cool! if you right click on any host, scapy will scan for port 80,22,21,23,25 and 443.
I think it's more useful the 2D output, but the 3D is so cool...
You can download scapy, from http://www.secdev.org
Let's do a basic traceroute:
>>> mytrace,err = traceroute (["www.google.com"])
And the classic output is this:
>>> mytrace.show()
216.239.51.99:tcp80
1 192.168.1.1 11
2 87.219.30.1 11
3 10.255.136.254 11
4 10.255.228.1 11
5 10.255.228.2 11
6 208.175.154.177 11
7 195.2.10.122 11
8 195.2.10.129 11
9 195.66.226.125 11
10 72.14.238.253 11
11 66.249.95.146 11
12 216.239.49.34 11
13 66.249.94.235 11
14 72.14.238.232 11
15 72.14.238.97 11
16 66.249.95.149 11
17 72.14.239.17 11
21 216.239.51.99 SA
23 216.239.51.99 SA
24 216.239.51.99 SA
26 216.239.51.99 SA
29 216.239.51.99 SA
Now if we want to create a 2D image of the results we just do this:
>>> mytrace.graph(target=">mytrace.svg")

Better for understanding ;)
And for last the 3D output:
>>> mytrace.trace3D()

Cool! if you right click on any host, scapy will scan for port 80,22,21,23,25 and 443.
I think it's more useful the 2D output, but the 3D is so cool...
You can download scapy, from http://www.secdev.org
Thursday, May 11, 2006
Extracting Deep Information
I was looking for a way, to get more information about my targets, something that could be useful
in a penetration test, one thing that is valuable are valid user accounts. So how can i have more
potential accounts? one way is harvesting email addresses from the search engines, this is old i wanted more; another way is to extract metadata from public documents of the target.
How can i accomplish that? Basically extracting MetaData information from the documents.
Metadata is literally "data about data", are information about another set of data. [wikipedia]
For example in the metadata we can found the Author Name, the software used with the document, who made the last change and even you can get the MAC address of the machine where the document was created.
Great, what we really want are usernames so the most valuable field is Author, so i thinked Why don't we use the power of google to find what public documents a company has, download them and extract the information we need?
To extract metadata i'm using the GNU libextractor it support
a lot of file formats. And recently I came across wvware it's used for access to Microsoft Word files, the difference is that with wv we can access to version control information, like the document that Michal Zalewski wrote about finding "recorded changes ranging from very minor (spelling, changed dates, slight reformatting, rewording to avoid being sued)", he did all the test on the Microsoft Website. lcamtuf-strikeout.
If you have any other idea please write me a lines to discuss the topic
That's all stay tuned.. :)
in a penetration test, one thing that is valuable are valid user accounts. So how can i have more
potential accounts? one way is harvesting email addresses from the search engines, this is old i wanted more; another way is to extract metadata from public documents of the target.
How can i accomplish that? Basically extracting MetaData information from the documents.
Metadata is literally "data about data", are information about another set of data. [wikipedia]
For example in the metadata we can found the Author Name, the software used with the document, who made the last change and even you can get the MAC address of the machine where the document was created.
Great, what we really want are usernames so the most valuable field is Author, so i thinked Why don't we use the power of google to find what public documents a company has, download them and extract the information we need?
To extract metadata i'm using the GNU libextractor it support
a lot of file formats. And recently I came across wvware it's used for access to Microsoft Word files, the difference is that with wv we can access to version control information, like the document that Michal Zalewski wrote about finding "recorded changes ranging from very minor (spelling, changed dates, slight reformatting, rewording to avoid being sued)", he did all the test on the Microsoft Website. lcamtuf-strikeout.
If you have any other idea please write me a lines to discuss the topic
That's all stay tuned.. :)
Subscribe to:
Posts (Atom)
Wfuzz 2.2.0 released
I'm pleased to announce a new version of WFuzz! Wfuzz has been created to facilitate the task in web applications assessments and it...
-
In the last few weeks everyone has been talking about Shellshock, the vulnerability affecting bash and having security ramifications everyw...
-
I'm pleased to announce a new version of WFuzz! Wfuzz is a tool designed for bruteforcing Web Applications, it can be used for findi...
-
In one of the latest penetration tests we faced a SSH server that was based in Maverick SSHTOOLS. The funny thing is that this server was ...