Hi, the new Backtrack 3.0 Beta is out there, the new version includes some of my tools, im very happy :P
Right now the tools included are Metagoofil , Subdomainer, TheHarvester (goog mails)
The new version claims to have these improvements:
* We will be releasing a ~ 1 GB USB / DVD image, as well as a stripped down 700 MB iso.
* Dual core issues have been fixed.
* Wireless card compatibility has maximised, and injection patches applied wherever possible.
* Xorg configuration scripts have been improved.
* Updated exploit repositories, updated metasploit exploit framework and dependencies.
* PXE network boot feature finally added (USB Version)
* PwnSauce Instant John the Ripper Cluster feature finally added (USB version)
* Compiz with ATI/Intel Drivers (USB version)
* Linux bt 2 6 21 5 #2 SMP
Download
And more security tools, that is what we want!!
Enjoy
Edge-security blog about Penetration testing, OSINT, security tools, and other interesting stuff.
Wednesday, December 19, 2007
Wednesday, October 17, 2007
Fist Conference - Barcelona
The next week (26/10/2007) i will be speaking at the FIST Conference about "Information Gathering" the speak will be based on Metagoofil. I will release a new version, with some fixes and improvements.
If you are in Barcelona, come and join us!
http://www.fistconference.org/barna.php
If you are in Barcelona, come and join us!
http://www.fistconference.org/barna.php
Thursday, September 6, 2007
Metagoofil
This tool is oriented to the extraction of metadata from files published in the domains of the target. It looks into the following type of files : PDF, PPT, DOC, XLS and MDB, and looks into different relevant fields, like "Author" or "Last Saved by".
The idea is to look into fields that may be used to get information about users, so can be used for brute-force attacks. This information can also provide windows domain users, or the methodology used by the company to generate user names.
Once the docs are identified, they are downloaded and analyzed. The information is presented in an HTML document. Please feel free to use this tool and don´t heasitate to send us your feedback.
Download: metagoofil-1.2.tar
The idea is to look into fields that may be used to get information about users, so can be used for brute-force attacks. This information can also provide windows domain users, or the methodology used by the company to generate user names.
Once the docs are identified, they are downloaded and analyzed. The information is presented in an HTML document. Please feel free to use this tool and don´t heasitate to send us your feedback.
Download: metagoofil-1.2.tar
Wednesday, August 29, 2007
Protocols, Data structures and File formats
Recently i discover the website Wotsit.org, is a place where you can find information of Data Structures, Protocols, File Formats, etc. It's a valuable resource for creating fuzzing tools, analyzing protocols, or develop a tool.
Really a must have in the security professional bookmarks!
Site: Wotsit
Enjoy
Really a must have in the security professional bookmarks!
Site: Wotsit
Enjoy
Sunday, August 26, 2007
Wfuzz, proxys and webserver scanning
Yesterday i was performing a pentest on a very big network. After struggling a bit i managed to upload files to a web server, an antivirus was running so many known tools didn't work, so it's time for more creativity. I pulled the http-proxy, a python based proxy developed by Edge-security, and compiled it into binary with py2exe, created an self-extracting zip, and uploaded to the server. I configured the proxy to listen on the port 53, as they leave that port unfiltered, neat :P
Well, so far so good, now i needed to know which machines were running webservers. I could have programmed a python scanner and upload it, but i was running out of time, so i went for wfuzz, the swiss knife for application testing (every body says their tool is a swiss knife), i used this command line to scan for web servers in the internal LAN through the proxy:
me ----> Server w/proxy ---->LAN
wfuzz -x serverip:53 -c -z range -r 1-254 --hc XXX -t 5 http://10.10.1.FUZZ
Some wfuzz switchs:
-x set proxy
--hc is used to hide the XXX error code from the results, as machines w/o webserver will fail the request (this is added on the new version).
With this command line, i will get every web server on the segment 10.10.1.X, i had to repeat this line for every segment the compromised server could reach, just that easy, fast and fun.
The http-proxy i used is part of the next framework that is being baked at Edge-security, stay tuned..
See you soon
Well, so far so good, now i needed to know which machines were running webservers. I could have programmed a python scanner and upload it, but i was running out of time, so i went for wfuzz, the swiss knife for application testing (every body says their tool is a swiss knife), i used this command line to scan for web servers in the internal LAN through the proxy:
me ----> Server w/proxy ---->LAN
wfuzz -x serverip:53 -c -z range -r 1-254 --hc XXX -t 5 http://10.10.1.FUZZ
Some wfuzz switchs:
-x set proxy
--hc is used to hide the XXX error code from the results, as machines w/o webserver will fail the request (this is added on the new version).
With this command line, i will get every web server on the segment 10.10.1.X, i had to repeat this line for every segment the compromised server could reach, just that easy, fast and fun.
The http-proxy i used is part of the next framework that is being baked at Edge-security, stay tuned..
See you soon
Wfuzz, proxys and webserver scanning...
Today i was performing a pentest on a very big network. After struggling a bit i managed to upload files to a web server, an antivirus was running so many known tools didn't work, so it's time for more creativity. I pulled the http-proxy, a python based proxy developed by Edge-security, and compiled it into binary with py2exe, created an self-extracting zip, and uploaded to the server. I configured the proxy to listen on the port 53, as they leave that port unfiltered, neat :P
Well, so far so good, now i needed to know which machines were running webservers. I could have programmed a python scanner and upload it, but i was running out of time, so i went for wfuzz, the swiss knife for application testing (every body says their tool is a swiss knife), i used this command line to scan for web servers in the internal LAN through the proxy:
me ----> Server w/proxy ---->LAN
wfuzz -x serverip:53 -c -z range -r 1-254 --hc XXX -t 5 http://10.10.1.FUZZ
Some wfuzz switchs:
-x set proxy
--hc is used to hide the XXX error code from the results, as machines w/o webserver will fail the request (this is added on the new version).
With this command line, i will get every web server on the segment 10.10.1.X, i had to repeat this line for every segment the compromised server could reach, just that easy, fast and fun.
The http-proxy i used is part of the next framework that is being baked at Edge-security, stay tuned..
See you soon, Laramies.
Well, so far so good, now i needed to know which machines were running webservers. I could have programmed a python scanner and upload it, but i was running out of time, so i went for wfuzz, the swiss knife for application testing (every body says their tool is a swiss knife), i used this command line to scan for web servers in the internal LAN through the proxy:
me ----> Server w/proxy ---->LAN
wfuzz -x serverip:53 -c -z range -r 1-254 --hc XXX -t 5 http://10.10.1.FUZZ
Some wfuzz switchs:
-x set proxy
--hc is used to hide the XXX error code from the results, as machines w/o webserver will fail the request (this is added on the new version).
With this command line, i will get every web server on the segment 10.10.1.X, i had to repeat this line for every segment the compromised server could reach, just that easy, fast and fun.
The http-proxy i used is part of the next framework that is being baked at Edge-security, stay tuned..
See you soon, Laramies.
Sunday, August 12, 2007
New tools and some docs..
Hi i'm back from the vacations, i will start posting more frequently than before, it's an objetive that i set.
Well let's move on the first post, it is about some new tools and documents from the last weeks.
Docs:
Blackhat and Defcon are over, and the presentations and whitepapers could be downloaded from here:
Blackhat: http://164.106.251.250/docs/netsec/bh2007/
Defcon: http://164.106.251.250/docs/dc15/
There are a lot of presentations, and some are really good.
Tools:
Nmap-SOC: First Nmap SOC release! Nmap 4.22SOC1
The new nmap version is available, with all the improvements proposed in the Summer Of Code (Google). Some of the highlights are:
-The UMIT graphical Nmap frontend is now included
-The port selection mechanism was overhauled
-Added the --reason option which explains WHY Nmap assigned a port status
-Integrated all of your 2nd generation OS detection submissions, increasing the database size by 68% since 4.21ALPHA4 to 699 fingerprints.
-Added --servicedb and --versiondb command-line options which allow you to specify a custom Nmap services (port to port number translation and port frequency) file or version detection database.
-In verbose mode, Nmap now reports where it obtains data files (such as nmap-services) from.
These are some of the more significant (at least for me), there are many more improvements on the release.
Information: http://seclists.org/nmap-dev/2007/q3/0030.html
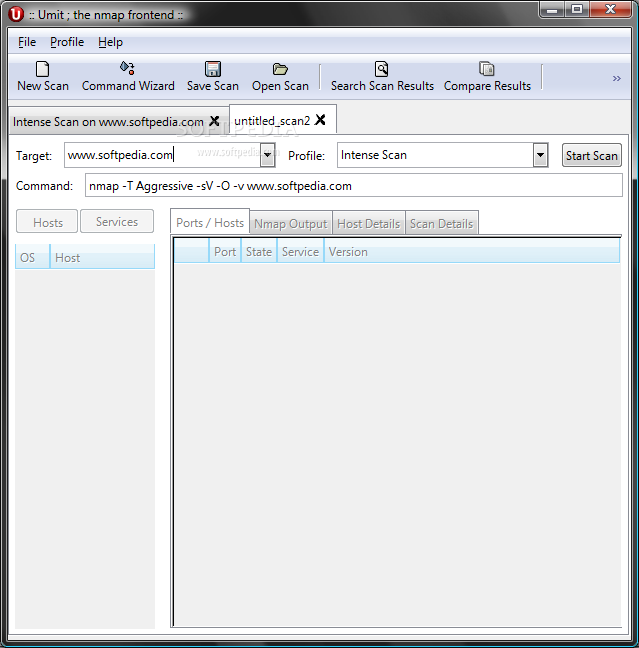
Umit: Nmap frontend.
Really a very good frontend, with a lot of functionalities, like comparing between different scans, saving scans, multiple tabs, profiles, information highlighting, etc. This project is sponsored by the Google Summer Of Code.
Install: http://umit.sourceforge.net/install.html
Blog: http://umitproject.blogspot.com/
Evolution: Massive information Gathering.
Evolution is a program that can be used to determine the relationships and real world links between different entities. Really it worths a try. I liked a lot the GUI, is still in beta stage, but is really awesome the interface.
Presentations: http://www.paterva.com/web/Evolution/Presentations/
Web: http://www.paterva.com/web/Evolution/

Immunity Debugger:
The new toy from Immunity guys, this is a new debugger oriented for vulnerability analysis, and security related task. It's programmed in python :), you can load python scripts to aid the analysis. Immunity says:
-A debugger with functionality designed specifically for the security industry
-Cuts exploit development time by 50%
-Simple, understandable interfaces
-Robust and powerful scripting language for automating intelligent debugging
-Lightweight and fast debugging to prevent corruption during complex analysis
-Connectivity to fuzzers and exploit development tools

Really a very good tool.
Information: http://www.immunitysec.com/products-immdbg.shtml
Announce: http://seclists.org/bugtraq/2007/Aug/0047.html
That's all for today :)
Well let's move on the first post, it is about some new tools and documents from the last weeks.
Docs:
Blackhat and Defcon are over, and the presentations and whitepapers could be downloaded from here:
Blackhat: http://164.106.251.250/docs/netsec/bh2007/
Defcon: http://164.106.251.250/docs/dc15/
There are a lot of presentations, and some are really good.
Tools:
Nmap-SOC: First Nmap SOC release! Nmap 4.22SOC1
The new nmap version is available, with all the improvements proposed in the Summer Of Code (Google). Some of the highlights are:
-The UMIT graphical Nmap frontend is now included
-The port selection mechanism was overhauled
-Added the --reason option which explains WHY Nmap assigned a port status
-Integrated all of your 2nd generation OS detection submissions, increasing the database size by 68% since 4.21ALPHA4 to 699 fingerprints.
-Added --servicedb and --versiondb command-line options which allow you to specify a custom Nmap services (port to port number translation and port frequency) file or version detection database.
-In verbose mode, Nmap now reports where it obtains data files (such as nmap-services) from.
These are some of the more significant (at least for me), there are many more improvements on the release.
Information: http://seclists.org/nmap-dev/2007/q3/0030.html
Umit: Nmap frontend.
Really a very good frontend, with a lot of functionalities, like comparing between different scans, saving scans, multiple tabs, profiles, information highlighting, etc. This project is sponsored by the Google Summer Of Code.
Install: http://umit.sourceforge.net/install.html
Blog: http://umitproject.blogspot.com/

Evolution: Massive information Gathering.
Evolution is a program that can be used to determine the relationships and real world links between different entities. Really it worths a try. I liked a lot the GUI, is still in beta stage, but is really awesome the interface.
Presentations: http://www.paterva.com/web/Evolution/Presentations/
Web: http://www.paterva.com/web/Evolution/

Immunity Debugger:
The new toy from Immunity guys, this is a new debugger oriented for vulnerability analysis, and security related task. It's programmed in python :), you can load python scripts to aid the analysis. Immunity says:
-A debugger with functionality designed specifically for the security industry
-Cuts exploit development time by 50%
-Simple, understandable interfaces
-Robust and powerful scripting language for automating intelligent debugging
-Lightweight and fast debugging to prevent corruption during complex analysis
-Connectivity to fuzzers and exploit development tools

Really a very good tool.
Information: http://www.immunitysec.com/products-immdbg.shtml
Announce: http://seclists.org/bugtraq/2007/Aug/0047.html
That's all for today :)
Tuesday, May 8, 2007
Metasploit GUI & Assistant
After a long waiting, a cool Metasploit GUI is available. In the development version of the metasploit is available the GUI with the new Metasploit::Assistant.
I think this is a great advance, and step by step the project is getting near the commercial options (Canvas, Core Impact). Right now Metasploit has 187 exploits, 106 payloads and many more
One great thing of this Framework is that runs on the Nokia 770/800, i hope for the GUI to run on the Nokia soon, it will be very easy to hack on the move, not typing in the mini X-term. Someone to port ruby-libglade and ruby-gtk2?
Next, Next, Next, Own3d ;)
For installing in Backtrack2 Final:
1-Download the following files:
ruby-gtk2
ruby-libglade2
2-Execute these commands:
# lzm2dir ruby-gtk2-0.16.0.lzm /
# lzm2dir ruby-libglade2-0.16.lzm /
# cd /pentest/exploits/framework3
# svn update
# ./msfgui
And here are some screenshots of the GUI running:




I think this is a great advance, and step by step the project is getting near the commercial options (Canvas, Core Impact). Right now Metasploit has 187 exploits, 106 payloads and many more
One great thing of this Framework is that runs on the Nokia 770/800, i hope for the GUI to run on the Nokia soon, it will be very easy to hack on the move, not typing in the mini X-term. Someone to port ruby-libglade and ruby-gtk2?
Next, Next, Next, Own3d ;)
For installing in Backtrack2 Final:
1-Download the following files:
ruby-gtk2
ruby-libglade2
2-Execute these commands:
# lzm2dir ruby-gtk2-0.16.0.lzm /
# lzm2dir ruby-libglade2-0.16.lzm /
# cd /pentest/exploits/framework3
# svn update
# ./msfgui
And here are some screenshots of the GUI running:




Sunday, May 6, 2007
Wfuzz update!
We did some bug cleaning, and some improvements to our wfuzz. Now it supports colored output on Windows machines!, we added support for fuzzing all GET and POST variables with one command, and we also tackle some errors.
If you find an error please send us an email, also if you have a new dictionary please help with the project and send it to us ;)
Check the new version: Wfuzz
If you find an error please send us an email, also if you have a new dictionary please help with the project and send it to us ;)
Check the new version: Wfuzz
My new Nokia 770!
Im very happy with my new Nokia 770, its an Internet Tablet that is between a mobile phone and a mini computer. It has an ARM processor, MMC memory, Wlan, Bluetooth, and an impressive 800x480 screen.
The cool thing is that is based on Debian Linux (Kernel 2.6.12). I bought it because i wanted to do some test and try to build a Security testing device, im developing a GUI based bluetooth scanner, and coding some Python tools. :)
There are available tools like: nmap, ettercap, aircrack-ng, kismet, rdesktop, and many more!
Here are some photos:



The cool thing is that is based on Debian Linux (Kernel 2.6.12). I bought it because i wanted to do some test and try to build a Security testing device, im developing a GUI based bluetooth scanner, and coding some Python tools. :)
There are available tools like: nmap, ettercap, aircrack-ng, kismet, rdesktop, and many more!
Here are some photos:



Tuesday, May 1, 2007
Wfuzz, the web bruteforcer is here...
It's been a while since the last tool were released, with deepbit we were working on a tool for Web Application testing, based on bruteforcing, very fast and useful. It can bruteforce GET and POST parameters, unlinked resources (directories, servlets, scripts), etc. It was used during our latest pentest and it shielded very good results. In the package is included a lot of dictionaries tailored for known applications like Weblogic, Websphere, Tomcat, IIS, Apache, Vignette, Fatwire, and many many more (thanks to Darkraver for letting us using Dirb's dictionaries).
Right now the ouput could be the console and a html file. The last one, is very useful for checking the results in the browser, and if you bruteforced a POST parameter, it will create a button in the Html that will send all the POST data, very cool.
If you are a pentester, you must have it ;)
Please check the Wfuzz page.
Right now the ouput could be the console and a html file. The last one, is very useful for checking the results in the browser, and if you bruteforced a POST parameter, it will create a button in the Html that will send all the POST data, very cool.
If you are a pentester, you must have it ;)
Please check the Wfuzz page.
Wednesday, April 11, 2007
Blackhat Europe 2007
Hi i'm back from Blackhat Amsterdam, and i really didn't liked it this time. I'm very disappointed with the organization, when i pay 1200 Eur i expect that the service and the organization of the event will be perfect (or at least very good), but this time it looked like a bunch of friends organized some conference without too much interest. Here is the list of things that i didn't liked:
0-Please stop giving for free those red bags, not even our girlfriends use them, they are totally ugly.
1-This year they didn't gave books, only the Cd-rom. (the book was ok, because you can take notes, read a slide that you miss, etc).
2-The organization wanted that the public use their laptops to read the cdroms, but in the conference room there were few sockets.
3-The lunch was a nightmare, the people had to wait in a queue to enter the restaurant, then make a queue to serve the food. Really a mess...
4-There were zero support for the speakers, some speakers had problems and there were nobody from the organizations to help them. For example one speaker had the audio
very low, and the public hardly heard him, nobody helped him until one person went outside to search for someone of the crew to fix the problem. Other speaker had a problem with his laptop socket and again, nobody from the crew was there.
5-The Microsoft party was a shame in comparison with 2006. Prefixed drinks, small place, it was more like a reunion in the house of a friend than a party :( (i think they spend all the budget in Windows Vista Marketing) ;)
6-The place was very small, and it was difficult to move when all the people was in the lobby.
7-There were coffe service with some food, but it was difficult to have a glass of water. Coffe a lot, water none.
That's all my thoughts, if they want to charge 1200 Eur, for the conference they have to mantain a quality level. From this year experience i don't recommend Blackhat Europe the next time.
If you have any question about blackhat, please let me know..
0-Please stop giving for free those red bags, not even our girlfriends use them, they are totally ugly.
1-This year they didn't gave books, only the Cd-rom. (the book was ok, because you can take notes, read a slide that you miss, etc).
2-The organization wanted that the public use their laptops to read the cdroms, but in the conference room there were few sockets.
3-The lunch was a nightmare, the people had to wait in a queue to enter the restaurant, then make a queue to serve the food. Really a mess...
4-There were zero support for the speakers, some speakers had problems and there were nobody from the organizations to help them. For example one speaker had the audio
very low, and the public hardly heard him, nobody helped him until one person went outside to search for someone of the crew to fix the problem. Other speaker had a problem with his laptop socket and again, nobody from the crew was there.
5-The Microsoft party was a shame in comparison with 2006. Prefixed drinks, small place, it was more like a reunion in the house of a friend than a party :( (i think they spend all the budget in Windows Vista Marketing) ;)
6-The place was very small, and it was difficult to move when all the people was in the lobby.
7-There were coffe service with some food, but it was difficult to have a glass of water. Coffe a lot, water none.
That's all my thoughts, if they want to charge 1200 Eur, for the conference they have to mantain a quality level. From this year experience i don't recommend Blackhat Europe the next time.
If you have any question about blackhat, please let me know..
Saturday, January 27, 2007
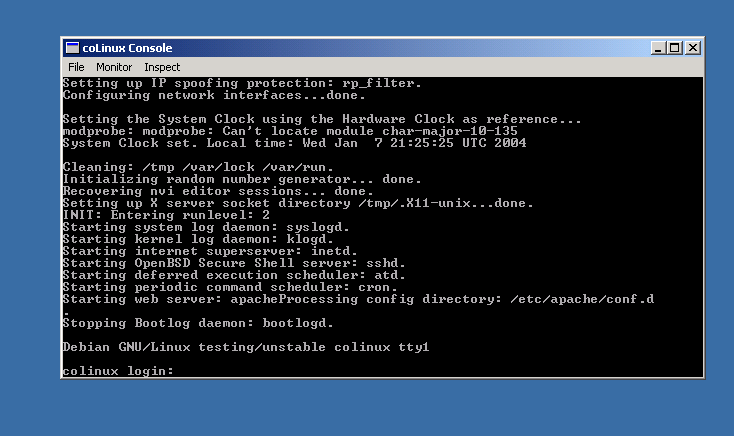
coLinux - Cooperative Linux


Some time ago i switched from Ubuntu to Windows XP (in my work computer), mostly because it made my work easier and faster ,but i always missed the linux command line and all the tools. I tried Cygwin, it's not too bad but still is not Linux. Yesterday a co-worker (Ruben) showed me coLinux:
From the coLinux site:
Cooperative Linux is the first working free and open source method for optimally running Linux on Microsoft Windows natively. More generally, Cooperative Linux (short-named coLinux) is a port of the Linux kernel that allows it to run cooperatively alongside another operating system on a single machine.
In short words, it's like Vmware, Parallels, Virtual PC but free, lighter and faster. It take just 4 seconds to boot a debian sarge!!
So now i have a real full linux in my Windows environment :)
Right now there are available Debian, Fedora, Gentoo, Ubuntu, Mandrake and many more OS images.
Best of all you can start coLinux machine as a Windows service an access via SSH through your favorite Terminal emulator (Poderosa, Putty, etc).
Just Great..
coLinux official page
coLinux Wiki
But still not even Windows and Linux together, can beat the MacOs X ;)
There is nothing like MacOs X with Parallels, running windows applications directly in the Os X desktop. (Coherence mode)


Enjoy...
Thursday, January 11, 2007
MD5 and SHA1

The other day i needed to crack a MD5 string and i hadn't the Rainbow Tables at hand so a partner show me the web http://md5.rednoize.com. It is very cool, and it also support SHA1, and it looks like google :)
The web does:
-Plaintext --> MD5
-Plaintext --> SHA1
-MD5 --> Plaintext
-SHA1 --> Plaintext
In the future i will add more website that offer this kind of service.
Enjoy
Wednesday, January 10, 2007
SSH Dinamic Port Forwarding
This is a mind note, cause i always forgot the command to create a dinamic port forwarding through ssh. Suppose you want to navigate the web with your browser but you want that the browser connection is made by other machine that has sshd running. So you can access web pages as if from the other machine.
You need to create a connection to the sshd server with the parameter -D and the port number where the local machine will listen to forward the connections. Example:
command>ssh myuser@sshdserver -D 8080
Now you have to configure the web browser to use SOCK Host: localhost Port:8080
In windows you can use putty, and you have to configure
Connection->SSH->Tunnel
Option: Source Port = 8080
Destination: Dinamic
That's all
You need to create a connection to the sshd server with the parameter -D and the port number where the local machine will listen to forward the connections. Example:
command>ssh myuser@sshdserver -D 8080
Now you have to configure the web browser to use SOCK Host: localhost Port:8080
In windows you can use putty, and you have to configure
Connection->SSH->Tunnel
Option: Source Port = 8080
Destination: Dinamic
That's all
Email Harvesting
I made an update to an old but useful tool, "googleharvester". Now the tool also works with msn search. I ported the program to Python because i feel more comfortable with the language and i program faster ;)
You can download the tool: Here
Now the tool is called "theHarvester"
enjoy
You can download the tool: Here
Now the tool is called "theHarvester"
enjoy
Sunday, January 7, 2007
Ngsec - Game #3 - Brainstorming
Well another Web application hacking game from Ngsec, this time there were 5 levels. The difficulty was very hard at the 2 first levels, and very very easy in the last 3. The order of the levels should have been inverse :) . But with some patience and Mandingo's tips, i finished in 9 hours aprox (not in a row).
It's was good game to kill some time and program a little.
Try it and became a g00r00 ;)
Game #3
Some tips:
Level 1 - I become blind.
Level 2 - Timing, it's all about timing.
Level 3 - Too easy, no tips.
Level 4 - With the tips and clues in the game, plus some tampering should be enough.
Level 5 - Very easy, just google.
It's was good game to kill some time and program a little.
Try it and became a g00r00 ;)
Game #3
Some tips:
Level 1 - I become blind.
Level 2 - Timing, it's all about timing.
Level 3 - Too easy, no tips.
Level 4 - With the tips and clues in the game, plus some tampering should be enough.
Level 5 - Very easy, just google.
Subscribe to:
Comments (Atom)
Wfuzz 2.2.0 released
I'm pleased to announce a new version of WFuzz! Wfuzz has been created to facilitate the task in web applications assessments and it...
-
Hi, this time i will post a brief entry about Oracle Forensics, when we talk about Oracle Forensics we are talking about David Litchfield , ...
-
I'm pleased to announce a new version of WFuzz! Wfuzz is a tool designed for bruteforcing Web Applications, it can be used for findi...
-
I'm pleased to announce a new version of WFuzz! Wfuzz has been created to facilitate the task in web applications assessments and it...
